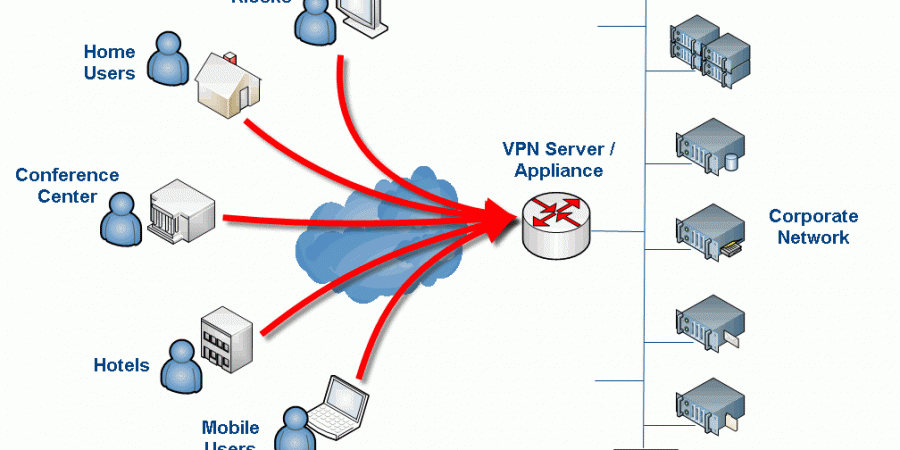
The current state of the world has caused some unique stresses on IT infrastructure. For IT departments servicing internal teams, remote access infrastructure in particular has felt the brunt of the blow. To that end, I spent a couple of weeks testing out enterprise VPN solutions.
I work on Azure Tenants that utilize multiple subscriptions in their design. I wanted to centralize my Azure Automation work and use a single Automation account. By default, I found that powershell scripts I fired off from Azure Automation work within the subscription that the Automation account was created within. But business requirements necessitate multiple […]
I have been using Powershell to manage pieces of Azure on and off for about a year and half now. I had heard tell of Azure Automation but never really had a good reason to justify spending the time climbing that particular mountain (hill really…). Then the request came through… let’s scale AzureSQL databases up […]
A colleague of mine recently solved one of the biggest pain points I have dealt with regarding Office365 – that is, Microsoft’s seemingly hit-or-miss modern authentication. Symptoms look like this: 1. Outlook client can’t connect and/or authenticate for end-users 2. Turning on Azure MFA for an end-user ruins their life (and yours) because all office […]
The Event Viewer is a very useful tool however, like any log management solution, the biggest hurdle can be filtering out the noise and returning only the meaningful log data that you care about. This is a follow-up on a previous article which can be viewed here: Finding Human Logins in the Windows Event Viewer […]
I have written articles on how to start using RealmD and SSSD for integrating ubuntu into a windows network. However, prior to that I wrote an article on using PBIS. RealmD and SSSD is, by far, the superior method IMHO and experience, so for all of those folks that want to switch, you probably want […]
For this tutorial I will be walking through how to use a tool called Realmd to connect an Ubuntu Server or Ubuntu Desktop system to a Windows Active Directory Domain. In the past I wrote an article talking about how to use Powerbroker Identity Services to do the same thing, but the scope of the […]
One of the things I wanted to get from my OpenVPN Access Server was a usage report that would be emailed to me regularly. OpenVPN Access Server writes such logs to a file in /var/log on Ubuntu and Debian based systems. However it also writes a lot of other things. So I first started by […]
You have two servers that both run linux. An origin server and a target server. You want to open up an SSH connection as the root user from the origin server to the root user account on the target server. Furthermore, you do not want to be prompted for a password but you still want […]
Do you work with MySQL? I do… quite a bit. Do you often script stuff on your server to make your life easier? I do that as well… quite a bit… Are you including your database user account and password (or worse… your mysql instance root user account and password!) in plain-text in your script… […]
If you haven’t use Filezilla Server before it is a pretty decent and easy to manage FTP/FTPS solution. While I don’t care for the Filezilla client (for several reasons, one of them being that it stores saved passwords in plaintext on your machine), the server software is okay… it runs nicely on Windows Server 2012 […]
I am not sure when OpenVPN added multi-factor support to their Access Server but I am thrilled that they did. It must have been recently (within the last few weeks or months) as I was using OpenVPN Access Server about 4 months ago as a temporary solution while my main solution was down and it […]
After having already gotten a full page into writing a walkthrough (not to mention hours already spent with Authy) I found out that Authy will NOT WORK with OpenVPN and LDAP authentication unless the folks at Authy customize the ldap module for you. Which requires enterprise support, at a retail price of $500/month! Which was […]
INTRODUCTION I wrestled with getting OpenVPN to work with Microsoft Active Directory authentication better part of 2 days. I was surprised that it was so hard to find a straightfoward tutorial on the topic that actually worked! I had to do a lot of Google-Fu and look at many different pages to put together what […]