I won’t go into great detail here but in short, if VSSAdmin is not letting you delete shadow copies and is throwing this message: Error: Snapshots were found, but they were outside of your allowed context. Try removing them with the backup application which created them. There is another (less safe…) program called DiskShadow which […]
I regularly use the Microsoft Windows sysprep tool to create template Windows Server 2012 R2 systems for wider deploy using cloning. Sysprep is used to modify a pre-configured Windows system and create an image or “template” so that you can create unique copies of it for faster system deployment. Failure to use syprep before cloning […]
I will keep this short and sweet. We have servers in our environment that have multiple IP addresses assigned to a single NIC. That’s normally just fine. However on occasion I will have very strange issues occur where essentially all networking appears to be working and yet web browsing won’t work. I can ping my […]
One of most difficult things to find (imho) is information about API and Service URL’s for just about any and all applications. Microsoft is better than some (Dell, I am looking at you…) but it can still require some metaphorical google search back flips to get to the right information. That said… I wanted to […]
The Event Viewer is a very useful tool however, like any log management solution, the biggest hurdle can be filtering out the noise and returning only the meaningful log data that you care about. This is a follow-up on a previous article which can be viewed here: Finding Human Logins in the Windows Event Viewer […]
One of the items I had to do a bit of digging to find was the location of the startup folder for all users. If you aren’t familiar with the “startup” folder on your system I will explain it briefly. The startup folder is a place you can put executable files (.exe), batch files (.bat), […]
Hyper-V Dynamic Memory Allocation strikes again… I have decided to no longer use Dynamic Memory Allocation on any of my virtual machines. It is a fine idea in theory but it is extremely buggy and I am not sure how it made it into a production OS… What’s the issue this time around? This is […]
I recently setup a new secondary windows domain. All of the users are logging in remotely via a VPN connection and their workstations belong to a different, separate domain… I quickly found myself having to regularly administer accounts… What I needed was a password self-service tool so users could take care of simple things like […]
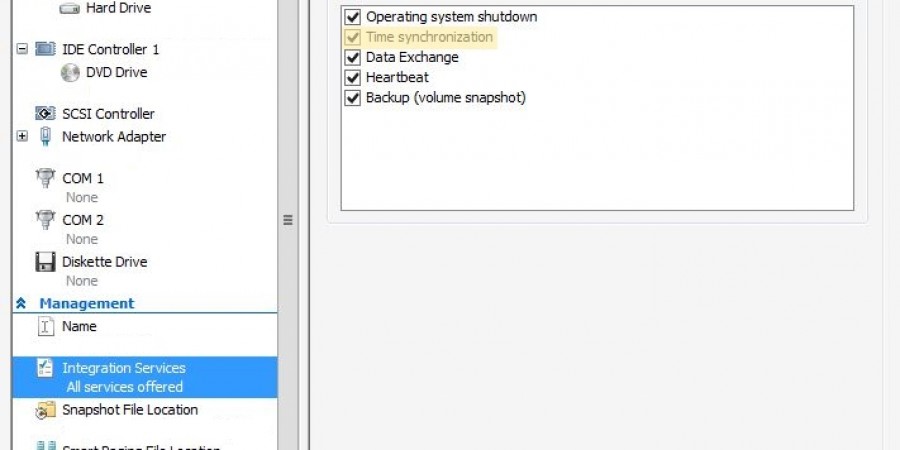
Ran into a fun issue today… I had a pair of Server 2012 R2 servers in a remote office that refused to sync the proper time for their clocks. No matter what I did they were always off by five minutes. One of them was a domain controller for the office. In the process of […]
One of my glorious privileges in IT is managing and enforcing security policy for the company I work for. Being a windows shop, one of the primary tools I use to that end is Group Policy. For those of you not familiar with Group Policy, it is Microsoft’s gift (and sometimes curse) to admins such […]
Today I am working on setting up a BackupPC server to take remote internal centralized backups of some of our other servers on the cheap. I already had BackupPC installed and the basics configured but I needed to add a new drive to the system (for additional backup data storage) and I also needed to […]
So you have just built your brand new Server 2012 box and need to download and install some software to get it up and running for the intended user. You open up IE because that is the only browser installed on a new box and hop on over to the download site, click the link […]
The company I work for has some rather remote offices and we are in the process of virtualizing some of our infrastructure components, particularly our remote domain controllers. I have done a remote DC deployment in one of our other foreign offices and the replication of the Domain took quite a while. In that case, […]