I am not sure when OpenVPN added multi-factor support to their Access Server but I am thrilled that they did. It must have been recently (within the last few weeks or months) as I was using OpenVPN Access Server about 4 months ago as a temporary solution while my main solution was down and it did not have Multi-Factor built-in. All I have to say is, THANK YOU!
I have been wrestling with Multi-factor solutions like Authy on the Community Edition of the server (Because Authy doesn’t even begin to work with OpenVPN Access Server) and was about ready to pursue trying out DUO with Access Server. Well… when I got into the Admin Web GUI for Access Server I discovered that there were options for turning on Google Authenticator built right in now. Skeptical as I was, I gave it a go anyhow. Up until now the only implementations of Google Authenticator with Access Server or Community Edition were little more than complex hacks. No longer though! It works, and it works beautifully. Because Access Server includes a Client Portal where users sign-up and download the client software for their machines, OpenVPN was able to streamline the Authenticator setup right into the client web portal. Furthermore, rather than having the user try to combine their password (which is hopefully complex) with their rotating PIN on the fly… i.e. typing in their credentials as USERNAME PASSWORD-PIN – which is a pain and undoubtedly leads to a rise is mis-authentications, OpenVPN uses a separate input box. THANK YOU!
So, what does this mean? Easy Multi-Factor Authentication that is very affordable. If you only need two concurrent connections the whole setup is actually free making it perfectly accessible for small business. Google Authenticator is free, as in free and OpenVPN Access Server is pretty affordable if you need to buy licenses for more concurrent connections. Anyhow, here is a picture of the setup screen (it is painfully simple!):


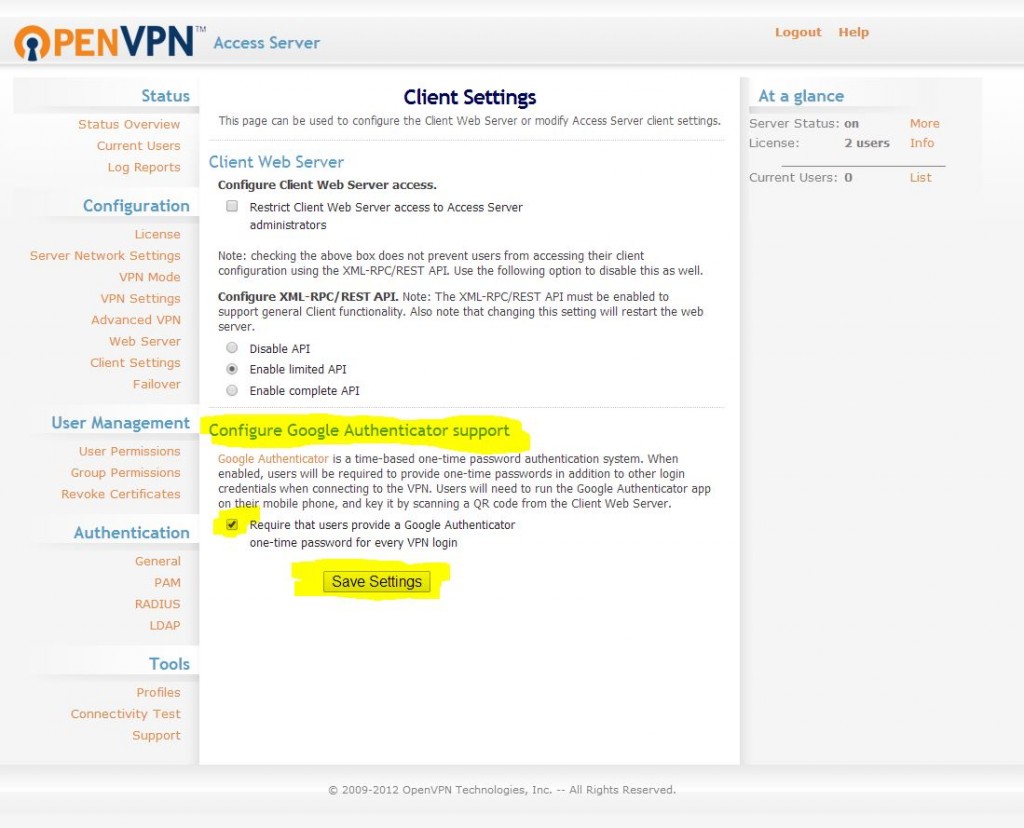
i just bought openvpn access server from AWS market (https://aws.amazon.com/marketplace/pp/B00ECFQMOC/) now i can not install google authenticator after i check box at “Configure Google Authenticator support” but still cannot establish vpn+google authenticator please help me how to configure it
many thanks
Let me take a look at what version we have setup in our environment and see if it matches what is being used by AWS. (which appears to be using 2.08)
On your side, I would recommend that you first (if you haven’t already) get VPN working without any of the google authenticator options enabled. So just use a username and password for testing.
If you can confirm you have that working first and can register a new user in that manner than that is a great start.
If you can also (if you are able from a security standpoint) share a bit more about what the end goal of your setup is that would be good. Also, if you can share some other particulars about your environment (like, for example, are you using Microsoft Active Directory or another LDAP solution for the user account management on the backend or are you just using OpenVPN Access server to setup user accounts). This is all useful information.
Kind Regards,
Nathan
Googleauth is using time based codes so the time on your VPN server in AWS, the time on your PC where you are running the openvpn connect client and the time on your phone where you are running the google auth app all need to be in sync.
You should run ntp on the openvpn AS server to keep the server in sync with an atomic clock and use the settings->sync on the google auth app to keep those in sync. Then you just have to make sure your PC is in sync with these times.
Not sure how it deals with the situation if you are in mainland Europe and using the AWS EU West data centre in Dublin as the server time would then be out of sync.
“Time Zone” differences shouldn’t matter. The systems are all aware of timezone difference. The actual time “sync” though does matter. Just find an NTP server near you (they are all over the globe) and sync to it and you should be good. Hope this clarifies.
When I check AutRequire that users provide a Google Authenticator one-time password for every VPN login, it is showing- Google Authenticator must be set for vpn access in the client side. Please help me out.
Yes, first time users have to go through a registration process on your openVPN web portal. They do this by visiting the client portal at the public IP address of your openVPN server. They sign-in with their username and password credentials and then will be redirected to a page with a QR code they can use to send the Google Authenticator token to the APP on their smartphone. This effectively pairs their smartphone with their user account for OpenVPN and whenever they need to login to OpenVPN they will have to have their smartphone… thus making it effectively a hardware token and a “second factor” for authentication. (Something you know (password) and something you have (your phone))… Hope this helps make sense 🙂
Google Authenticator works with OpenVPNConnect client , but not OpenVPN GUI client. OpenVPN GUI client does not support multifactor auth.
Are you using OpenVPN Community edition or the paid OpenVPN “Access Server”? This article is specific to the paid version “Access Server” and the two systems differ quite a bit. Hope this clarifies/helps. I am currently using Access Server and the Windows GUI OpenVPN client application works quite well with Google Auth as does the command line version of the windows client.
Tried to configure Google Auth, on OpenVPN access server, as per the above “client settings” as shown above. Sadly this only blocks users and never beings up the “client web server” so I can scan the QR code.
Can anyone tell me how to get the rest of the configuring on the server? I have downloaded all needs software to my cellphone. It can’t capture the OpenVpN barcode that is never displayed
I can’t get the openvpn GUI client to work, but I can connect using the web address of the OpenVPNas and then selecting LOGIN. After scanning the QR code displayed on the login page it sets up that login to my phone and then subsequent login/connect to the OpenVPNas site will ask for Username and password and then the next screen will ask for the authentication code and that works. You may need to change the authentication method to local to get it all working.