I finally found a few minutes to write up a short how-to on getting your Chinese Xiaomi Mi3 Smartphone rooted, westernized, and cleaned up! To make your life much easier, I have actually written a couple of scripts that can be used to remove all of the Chinese bloatware from the phone, install the Google […]
Update 3/31/2016 – PBIS doesn’t work well as of late and this method has been superceded by this article here: http://www.kiloroot.com/add-ubuntu-14-04-server-or-desktop-to-microsoft-active-directory-domain-login-to-unity-with-domain-credentials/ Update 5/18/2014 – I created scripts to automate 90% of this process. I still recommend you read this post before just jumping in and using the scripts so that you know what exactly it […]
The Heartbleed bug is what I would professionally classify as seriously scary stuff. Basically there is some kind of heartbeat functionality built into OpenSSL. Often, in tech talk, this kind of thing is used for remote service monitoring (i.e. if I have a pulse my service is at least up). In this case, I am […]
What is a Ram Disk you ask? Simply put, you carve out a piece of your system’s RAM and use it as a normal file system. But you probably have some more questions… Why would I want to do this? Simply put, RAM is very fast. Faster than most (any?) SSD drive. So if you […]
Google Authenticator, and (all?) other rotating-pin multi-factor authentication systems, rely on the clock on the token device (in this case your smart-phone or tablet) and the authenticating system (in this case the OpenVPN server). If the clocks are different by more than a few seconds or so, it will break your authentication.
I thought I would put this together quickly because in typical Linux fashion something that should be straightforward isn’t… Node.js – I am still not sure what it is :), however I am in the process of setting up drupalchat on one of my sites and when I tried using it with the AJAX option, […]
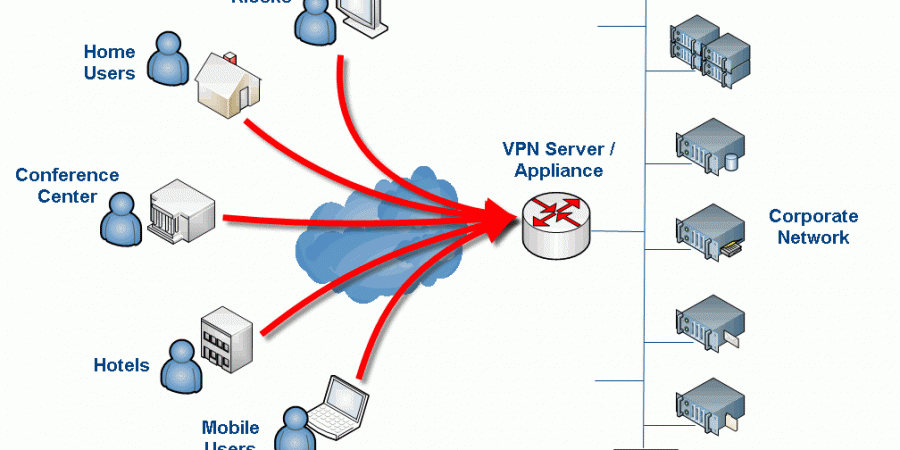
I am not sure when OpenVPN added multi-factor support to their Access Server but I am thrilled that they did. It must have been recently (within the last few weeks or months) as I was using OpenVPN Access Server about 4 months ago as a temporary solution while my main solution was down and it […]
After having already gotten a full page into writing a walkthrough (not to mention hours already spent with Authy) I found out that Authy will NOT WORK with OpenVPN and LDAP authentication unless the folks at Authy customize the ldap module for you. Which requires enterprise support, at a retail price of $500/month! Which was […]
INTRODUCTION I wrestled with getting OpenVPN to work with Microsoft Active Directory authentication better part of 2 days. I was surprised that it was so hard to find a straightfoward tutorial on the topic that actually worked! I had to do a lot of Google-Fu and look at many different pages to put together what […]