INTRODUCTION
I wrestled with getting OpenVPN to work with Microsoft Active Directory authentication better part of 2 days. I was surprised that it was so hard to find a straightfoward tutorial on the topic that actually worked! I had to do a lot of Google-Fu and look at many different pages to put together what I needed to get this done. So… to hopefully save myself and others some future headache. I endeavor to put most of it all together here. This guide assume a few things about the audience though that you should know up front…
First, you have a basic understanding of networking concepts like IP addresses, nic cards, etc. and more specifically an idea of how all of that works in linux.
Second, you know what a VPN connection is and have some basic understanding of the concepts surrounding VPN’s.
Third, you have a decent handle on working with linux (in this case ubuntu) from the command line. If you are setting up a VPN server in an enterprise environment you should most likely be doing so on the server version of your chosen OS for reasons I won’t go into here. In 99% of cases that means working from the command-line or maybe a web based GUI at most.
Fourth, you know how to use a command-line based word processor like VI, VIM, or NANO. I use “VIM” and it will be in my commands throughout. Feel free to substitute whatever text editor you are comfortable with. As a small aside, if you have just started getting your feet wet with linux and haven’t started learning how to use a command-line based text editor you are really hurting yourself. It can seem a bit daunting at first but once you get the basics down (which takes about 30 minutes) you can do most of what you need to do. You don’t need to be a pro at VI to administer a ‘nix box but just ignoring it because it seems complex (which I tried for a long time) isn’t the best approach.
Pre-Requisites for Getting this setup:
1. You have sudoer / root on the box
2. Your candidate server has internet access (we are going to have our clients tunnel all of their traffic through this server, so if they want internet access, the box must have it, you also need access to download packages from the repository to get this going).
3. A Microsoft Active Directory Domain Controller server (I am working with Server 2008R2 boxes) that the OpenVPN server can see on the network and talk with or at least has TCP/UDP port 389 open between them. You need to know the IP of the DC (Domain Controller).
4. A domain user account with a non-expiring password. (This is the service account that our OpenVPN box will use to query active directory, it can be any low-privilege user account and I recommend one with a non-expiring complex password).
5. Patience… a lot of patience…
6. Port XXXX (pick an open port above 1000) is open for bi-directional UDP traffic between your OpenVPN server and the outside world (or wherever else you are trying to create a VPN connection from). I recommend changing from the default port for security reasons.
7. I am working off of an Ubuntu Server box – if you are newer to linux, you definitely should be to. Ubuntu is extremely well supported, stable, and fairly easy to work with. I use a package manager to install stuff as much as possible as it really is much less trouble than compiling from source. I am not anti compiling from source, but prefer the path of least resistance when possible.
Okay… let’s dive in!
CONTENTS
- Introduction, Pre-Req’s, Table of Contents
- Getting Your Firewalls Configured
- Install OpenVPN, Configure Easy-RSA & Setup CA
- Create Certificates
- Configure OpenVPN Server
- Client Configuration and Installation
- Setting Up OpenVPN with Active Directory Authentication
- Route ALL Traffic Through an OpenVPN Tunnel

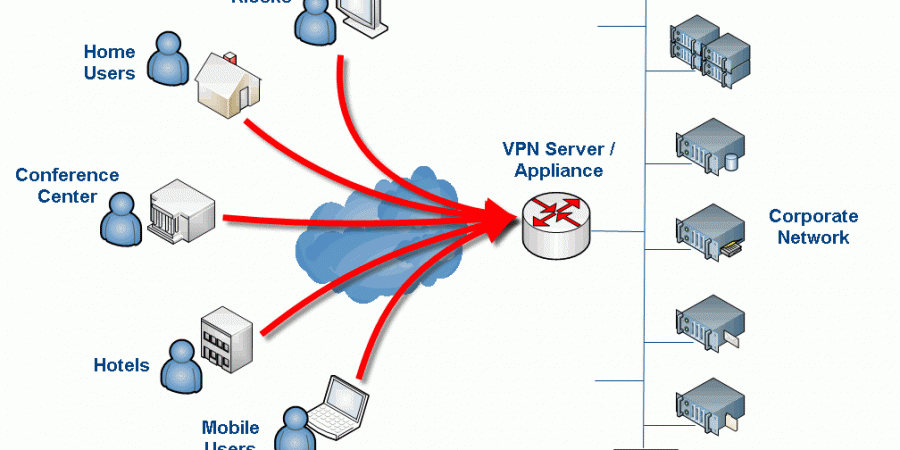
Just an FYI, one of the commands after the second to last reboot prevents any connection to the Linux server
That’s interesting, do you know which command or configuration item is killing the connection? I am wondering if I fat-fingered something somewhere in the write-up. It has been a while since I worked on this. I know when I was testing that VPN connectivity still worked and that the final result was “no split-tunneling” i.e. proxy client machines had all traffic forced through the VPN tunnel. What I am not sure is if I somehow broke SSH connectivity but didn’t realize it because I was working on the machine directly (i.e. not remotely via SSH).
If you can shed some light on this so I can fix the write-up that would be awesome. Hate to have anyone breaking things on there end 🙂
Thanks for the heads up!
Yeah so basically for some reason, doesn’t make sense to me, adding that entry into the iptables and setting the file to load upon restart locks out any connection in, the system i implemented this in is in azure so remote access is the only option, it’s most probably a requirement to add an accept for SSH?
adding the entry without setting the file to load upon restart doesn’t cause any issues (as far as i can tell haven’t checked thoroughly enough)
great post, really love it!
greets, Wilfried
I did it but start openvpn is failed .
openvpn-auth-ldap plugin is 2.03 and download using “yum instal openvpn_auth-ldap.x86_84” on Centos 6
Thanks for this guide. I suggest copy and past attributes from AD directly into “/etc/openvpn/auth/auth-ldap.conf” . This was my issue. Good luck
This saved me a ton of time. Thanks for taking the time to post it.
Just wonder is there a way to secure client certificate from being compromised and used from another PC ?
cp server.crt server.key ca.crt dh1024.pem ta.key /etc/openvpn/
here should dh1024 should be changed to dh2048 i believe
Great article! Helped me a lot! Little supplement: Add the following to your server.config:
push “dhcp-option DOMAIN fqdn.yourADDomain.com”
Otherwise a had to use the fullname e.g. servername.fqdn.mydomain.ch to contact my internal infrastructur.
Thanks! Appreciate the tip as well 🙂 – Sure it will help others. OpenVPN Community Edition is honestly a bit of a bear. I finally gave up and just moved to the paid version (which is relatively cheap vs. other similar solutions) which is like a completely different product from an administrative perspective. The thing I really needed was two-factor authentication and the community edition (at the time) was very hard to get setup with this.